Cyber security experts say they have discovered a new malware campaign targeting supporters of protests in Iran, as tension between Washington and Tehran simmers.
The malware has been called “Crescent Harvest”, according to the cyber security and data protection company Acronis, which first noticed the programme in early January, as demonstrations spread across Iran.
“What makes it particularly noteworthy is how methodical and patient the attackers are,” said Subhajeet Singha, a senior security researcher for Acronis. He added that the people spreading the malware appear to be trying to form relationships with people outside Iran who are supportive of demonstrations inside the country, establishing a rapport and then sending the malicious files.
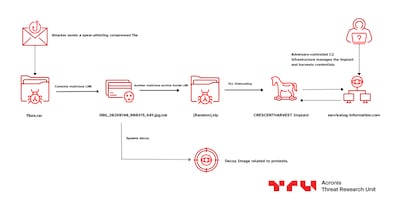
“It's the digital equivalent of a con artist building a rapport before closing the deal,” he explained. “The victim eventually receives what looks like a bundle of protest materials – photographs, videos and a report written in Farsi discussing recent developments in Iran's rebellious cities.”
Buried within the files, according to Acronis, is nefarious software that harvests passwords and allows cyber criminals to gain remote access to the system. Mr Singha said the malware is proving difficult to eliminate.
“Even if someone suspects something and tries to isolate their computer, the moment it goes back online, the attackers regain a foothold,” he said, adding that the malware effort takes advantage of trust and timing, especially among those seeking to gain information and appear to be sympathetic to demonstrators in Iran.
Acronis told The National that it was able to identify Crescent Harvest during “routine threat hunting” by its research teams. Eliad Kimhy, senior researcher at Acronis, said he expectsthe perpetrators are looking to infect computers used by journalists, activists, politicians and dissidents.
Mr Kimhy said the goal seems to be information theft and long-term espionage. “The level of technical sophistication employed in this campaign would make it challenging for an untrained individual to detect or prevent, and the attacker has put a lot of effort into making this attack as evasive as possible,” he said.
He added that in addition to cybersecurity software, people need to make sure they're being extra vigilant when clicking links or downloading files from people and entities they're not familiar with. Acronis said the use of Farsi in this malware, which is sent via email, text message and chat apps, strongly suggests that it originates from actors sympathetic to the Iranian regime.
“To the victim, this archive seems to contain an update from the front line of the protests in Iran, including a number of videos and images of the ongoing protests, and a document named گزارش.docx (report.docx in Farsi),” a news release from Acronis read.
Though Iran has been significantly weakened by several decades of sanctions, its cyber crime efforts have gained strength and captured the attention of cyber security officials in the US. In June, following US strikes on Iranian nuclear facilities, the US Department of Homeland Security warned citizens that retaliation may come in the form of cyber attacks.
According to a 2025 cybersecurity report from Microsoft, Iran has most frequently targeted Israel, the US, the UAE and India with attempted cyber attacks.
Also late last year, Brett Leatherman, who leads the FBI’s cyber operations division, said a hypothetical cyber attack from Iran on US technology systems, data and infrastructure would probably be considered an act of war, though he added that Iran seemed to realise that such an attack would trigger a response that would be akin to “mutually assured destruction”.


