- Israeli tanks push deeper into Jabalia in northern Gaza
- Netanyahu says Israel has killed Nasrallah's successors
- UN chief writes to Netanyahu over proposed bills to outlaw the UNRWA
- Hezbollah says it supports ceasefire
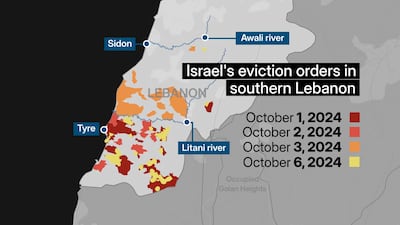
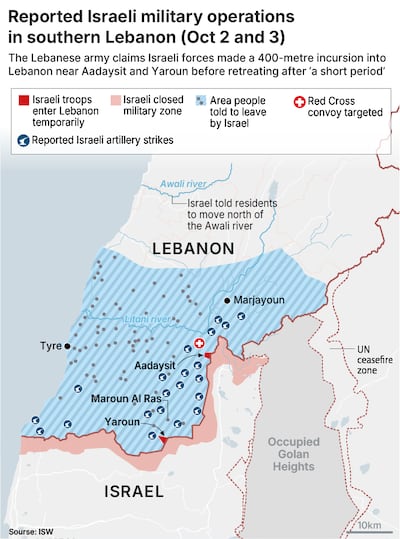
- UN intervention needed to stop Lebanon becoming a new Gaza, says EU’s Borrell
- At least 41,965 killed in Gaza and 2,083 in Lebanon since October 7, 2023
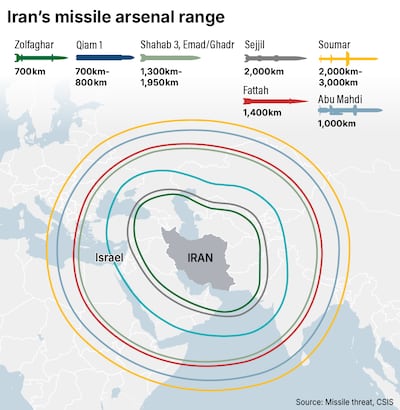
Planes rerouted after Iran's missile attack on Israel
Updated: October 09, 2024, 8:46 AM